Our Blogs
- July 26, 2024 Beware the Bait: Protecting Yourself from Targeted Phishing AttacksThe digital age offers unparalleled connectivity and convenience, but it also presents new security challenges. Phishing attacks, including...By Admin
- July 21, 2024 Vendor Email Compromise: Don’t Let Your Dubai Business Become the TargetIn Dubai's bustling business world, working with vendors is essential. But what happens when that trust is exploited...By Admin
- July 16, 2024 Why You Need Mobile App Penetration Testing in the UAEThe UAE is a hub for innovation and technology, with a rapidly growing mobile app market. As more...By Admin
- July 11, 2024 Essential Office 365 Backup Solutions in DubaiBusinesses in Dubai rely heavily on Microsoft 365 for seamless collaboration and efficient workflows. However, protecting this critical...By Admin
- July 5, 2024 Top Antivirus Solutions for Dubai Businesses: Secure Your Data in a Digital AgeCybersecurity is no longer an option; it's a necessity. With cyberattacks on the rise globally, Dubai businesses of...By Admin
- June 28, 2024 How Cyberbullying Threatens Online Safety: Stay Safe with UAE LawThe internet has become an integral part of our lives, connecting us with friends, family, and information. But...By Admin
- June 24, 2024 Keeping Your Data Safe: A Look at Different Cybersecurity TypesCybersecurity involves keeping an organization, its employees, and assets safe from cyber threats in every possible way. With...By Admin
- June 20, 2024 Top Steganography Tools for 2024When you need to send secret messages without anyone suspecting, steganography is the way to go. It's like...By Admin
- June 18, 2024 Top 5 Strategies to Prevent Data Leakage in Your OrganizationData leaks are a constant threat in organizations. A data leak is when information is exposed to unauthorized...By Admin
- June 14, 2024 How App Permissions Can Compromise Your Data SecurityWe all love the convenience of apps. They keep us connected, entertained, and informed. But have you ever...By Admin
- June 12, 2024 Steganography: Hiding Information in Plain SightHave you ever thought there might be more to a picture than what you see? Or wondered if...By Admin
- May 31, 2024 How to Prevent Data Loss in DubaiDubai businesses handle a lot of important info, like customer details and finances. Keeping this data safe is...By Admin
- May 31, 2024 Best Anti-Phishing Solutions for Dubai CompaniesAs cyber threats continue to evolve, businesses in Dubai face increasing risks from phishing attacks. Cybercriminals use sophisticated...By Admin
- May 30, 2024 Intellectual Property Protection in Dubai: Protect Your Business IdeasIntellectual property in the UAE is very important for business operations and must be understood by every entrepreneur...By Admin
- May 30, 2024 What to Do After a Cyberattack?Seek a solution from a leading Cyber security Company in Dubai As more people and organizations use technology,...By Admin
- May 29, 2024 Stop Website Spoofers in Their Tracks: Domain Spoofing Protection Services in DubaiDubai's online world is a ground for innovation, but also cybercrime. One tactic fraudsters use is domain spoofing,...By Admin
- May 17, 2024 Cyber Incident Response Services in DubaiThe Critical Need for Effective Cyber Incident Response Cyber threats are an ever-present danger, with the potential to...By Admin
- May 16, 2024 Secure Your Office 365 Environment with Data Loss PreventionOffice 365 has become a cornerstone of modern business productivity, providing organizations with powerful tools for communication, collaboration,...By Admin
- May 15, 2024 Brand Impersonation Protection Services for Dubai BusinessesOffice 365 has become a cornerstone of modern business productivity, providing organizations with powerful tools for communication, collaboration,...By Admin
- April 29, 2024 Ransomware protection in DubaiWhat is a Ransomware Threat Dubai is now known as a growing center for innovation and technology. But...By Admin
- April 26, 2024 Data Loss Prevention and Security SolutionsThe Imperative of Data Protection Data is the lifeblood of businesses in the current digital age, propelling innovation,...By Admin
- March 14, 2024 Top Email Security Technologies for the EnterpriseEmail remains a fundamental communication tool for businesses worldwide. However, its widespread use also makes it one of...By Admin
- March 11, 2024 The Top Email Security Solutions for Office 365 UsersEmail remains a primary communication tool for businesses, making it a prime target for cyber threats. For organizations...By Admin
- March 9, 2024 Protection Offered by Email Security Against Different Attack VectorsEmail continues to be a primary means of communication for businesses globally, serving as a gateway to potential...By Admin
- March 8, 2024 Essential Precautions for Online SecurityCyber threats are evolving with increasing sophistication, making it imperative for organizations and individuals to adopt robust security...By Admin
- March 6, 2024 The Importance of Timely Security Patch ManagementAmong the various strategies employed to safeguard digital assets, timely security patch management stands out as a critical...By Admin
- March 5, 2024 Simple Steps to Secure Your Website: A Practical Guide for Business OwnersIn the digital age, a business’s website serves as its digital storefront, not just presenting the brand to...By Admin
- March 4, 2024 Securing Business Transactions: Best Practices for Online Payments and Financial SecurityOnline transactions are the mainstay of most businesses in the digital age, allowing them to expand their customer...By Admin
- February 26, 2024 Cybersecurity for Small Businesses: Big Threats and Budget-Friendly SolutionsIn an era where digital presence is nearly ubiquitous for businesses of all sizes, cybersecurity can no longer...By Admin
- February 24, 2024 Zero Trust Security: How Privileged Access Management Fits into the PuzzleThe Zero Trust model has emerged as a foundational principle, particularly in the face of evolving digital landscapes...By Admin
- February 22, 2024 Ensure your Emails are properly secured with 4 TipsCyber security attacks, are one of the most commonly occurring threats in the modern era. As our world...By Admin
- February 19, 2024 A Comprehensive Guide to Advanced Email Threat ProtectionEven in this digital age, email is still a vital tool for corporate communication around the globe. However,...By Admin
- February 15, 2024 Choosing the Right PAM Solution for Your Business: A Buyer’s GuidePrivileged Access Management (PAM) solutions have emerged as essential tools for protecting critical assets and managing the risks...By Admin
- February 14, 2024 A Comprehensive Guide to Cybersecurity for BusinessesCybersecurity has become a cornerstone of business operations, safeguarding sensitive data from the ever-evolving threats posed by cybercriminals....By Admin
- February 5, 2024 Advancements and offerings of ChannelNext in the cyber securityCybersecurity plays a crucial role in an era where digital connections and technological dependence are the norm. To...By Admin
- February 5, 2024 ATO- Account TakeoverHas Your Account Been Taken Over? How it works An account takeover attack is, as the name suggests, when...By Admin
- February 5, 2024 How should you evaluate a cyber security company in Dubai for credibility and expertiseTrusted cyber security company in Dubai can mean the difference between digital safety and vulnerability. This blog will...By Admin
- January 26, 2024 Services offered by Channel Next and its impact on the cybersecurityOrganizations want a trustworthy partner to help them manage the challenges of digital defense in the rapidly changing...By Admin
- January 22, 2024 A comprehensive guide on implementing DMARC effectivelyDMARC (Domain-based Message Authentication, Reporting, and Conformance) is a potent weapon in the toolbox against phishing and email...By Admin
- January 19, 2024 importance of Scalefusion in cloud securityAs businesses increasingly rely on cloud services in the era of digital transformation, the need for strong cloud...By Admin
- January 17, 2024 Role of Perception Point in Modern Cybersecurity StrategiesOrganizations demand new solutions to bolster their defenses in the changing landscape of cybersecurity, where threats continue to...By Admin
- January 11, 2024 Significance of DMARC in enhancing email securityEmail continues to be the main method of communication for both personal and corporate letters in the broad...By Admin
- January 9, 2024 An overview of various email security solutionsIt is critical to protect email as the main means of communication in the digital age, as it...By Admin
- January 9, 2024 Business Wi-Fi: Simple Tips to Keep Unwanted Intruders at BayIn the digital age, Wi-Fi has become as essential to business operations as electricity and running water. It...By Admin
- December 30, 2023 Smart Gadgets, Safe Living: How to Manage Your Smart DevicesAs smart gadgets become more and more integrated into our daily lives, it is important to make sure...By Admin
- December 28, 2023 Secure your online safety with the new approach of locking down your networkIt is imperative that we change our perspective on online safety in the digital age, as cyber threats...By Admin
- December 26, 2023 How to Keep Phones Safe and ProductiveEnsuring the safety and productivity of mobile phones is crucial at a time when they are essential tools...By Admin
- December 21, 2023 Why You Need a Unified Defense for Your DevicesIn an era dominated by digital connectivity, the proliferation of cyber threats necessitates a transformative approach to security....By Admin
- December 18, 2023 Keep your cloud secure with these essential tips for cloud safetyStrong cloud security is essential for protecting sensitive data and preserving operational resilience as more and more enterprises...By Admin
- December 15, 2023 Email Safety 101: Stop Hackers with These Easy StepsEmail still plays a major role in both professional and personal interactions in a time when digital communication...By Admin
- December 13, 2023 IoT Device Management: What It Is and Why You Need ItThe Internet of Things (IoT) has become an essential aspect of our digital landscape in the age of...By Admin
- December 7, 2023 How to Keep Your Computers and Phones SafeThe security of our computers and phones becomes a critical worry in a period where our personal and...By Admin
- November 30, 2023 Cybersecurity Best Practices for Remote Work EnvironmentsThe typical workspace has undoubtedly changed as a result of the paradigm shift toward remote work. This has...By Admin
- November 30, 2023 What is Cloud Monitoring Best practises for Complete visibilityThe adoption of cloud infrastructure has become essential for businesses looking to grow and develop in the constantly...By Admin
- November 29, 2023 Antivirus solutions for Laptops and Desktop ComputersIn the constantly changing field of cybersecurity, having strong antivirus protection is essential. Protecting laptops and desktop computers...By Admin
- November 25, 2023 How to Securely Access the Cloud: An All-Inclusive Guide to Cloud Security ServicesCloud computing has transformed the way businesses work, providing legendary flexibility, scalability, and efficiency. The convenience of cloud...By Admin
- November 22, 2023 5 Essential Cybersecurity Practices Every Business Should Implement5 Essential Cybersecurity Practices Every Business Should Implement A growing range of cyber risks confront organizations in an era...By Admin
- November 20, 2023 Top Tools and Practices for Application Security TestingIt is critical to have strong security. As more organizations in Dubai embrace technology, the requirement for robust...By Admin
- November 15, 2023 Top Cyber Threats Facing Small Businesses and How to Defend Against ThemSmall companies are the foundation of entrepreneurship and innovation. But because of their popularity, they are vulnerable to...By Admin
- November 14, 2023 UAE Penetration Testing Landscape: Who’s Leading the ChargeIn the short-growing international of enterprise and era, the United Arab Emirates (UAE) stands out as a prime...By Admin
- November 10, 2023 The Importance of Regular Security Audits and Penetration TestingHaving strong cybersecurity is essential, not just a choice. Since cyber threats are becoming more sophisticated, organizations need...By Admin
- October 23, 2023 Staying Ahead of Cyber Threats: UAE’s Top Endpoint Security StrategiesStaying Ahead of Cyber Threats: UAE's Top Endpoint Security Strategies Cybersecurity has grown to be of utmost importance to...By Admin
- June 7, 2023 Protecting Against Phishing Attacks: Types, Defensive Measures, and the Power of DLP SolutionsIntroduction: In today’s digital landscape, phishing attacks have become increasingly prevalent and sophisticated, posing significant risks to individuals and...By Admin
- February 24, 2023 DMARC Tester – DMARC Testing Methods ExplainedDMARC Testing is an essential part of your email authentication configuration because it makes sure your DMARC protocol...By Admin
- February 23, 2023 RevBits XDR Platform Brings Clarity and Responsiveness to Threat DetectionFrom antiquity to the present, every civilization has felt the need to develop a warning system to alert...By Admin
- February 22, 2023 What is ITSM? A Guide to IT Service ManagementWhat is ITSM? IT Service Management (ITSM) is a comprehensive approach to managing and delivering technology-based services that cater...By Admin
- February 17, 2023 Key Importance of Network Configuration ManagementWhether you’re running an enterprise in the IT, banking, or manufacturing sector or an insurance provider, your IT...By Admin
- February 9, 2023 Best Practices and Processes to Organize Your Work OrdersMost enterprises have a lot of equipment and assets that require routine maintenance, if it is done over...By Admin
- February 8, 2023 What is an Email Header Parser?An email header parser is a tool that can help you to parse email headers of a specific...By Admin
- February 7, 2023 RevBits PAM Provides Chameleon-Like AdaptabilityKey Points About the RevBits PAM Chameleon-Adaptability Cybersecurity solutions are constantly evolving to keep up with the ever-changing threat...By Admin
- February 3, 2023 SPF Format : SPF Basic & Advanced Formats ExplainedYou can send emails without using SPF or knowing about SPF format, but that won’t be safe. SPF adds...By Admin
- January 20, 2023 What’s New at ScalefusionAt Scalefusion, we are excited to ring in the new year with an interesting set of updates. Here’s...By Admin
- January 19, 2023 Best Asset Management in Work Order Tracking For 2023Many businesses lose productivity because of failing to track work orders. In order to maintain constant efficiency, work...By Admin
- January 13, 2023 Browser Security: Threats, Solutions, and User EducationWhat is Browser Security? The web browser has evolved from a mechanism for displaying text documents to the ubiquitous...By Admin
- January 6, 2023 How To Distribute Custom iOS AppsThe App Store empowers iOS users worldwide to discover a plethora of trusted apps for their personal and...By Admin
- January 5, 2023 DMARC SIEM IntegrationDMARC SIEM Integration is the process of connecting your existing SIEM solution to an additional system such as...By Admin
- January 3, 2023 Beware of these Holiday Phishing ScamsPhishing attacks are rampant now that the holiday season has begun. Cybercriminals are constantly looking for ways to exploit...By Admin
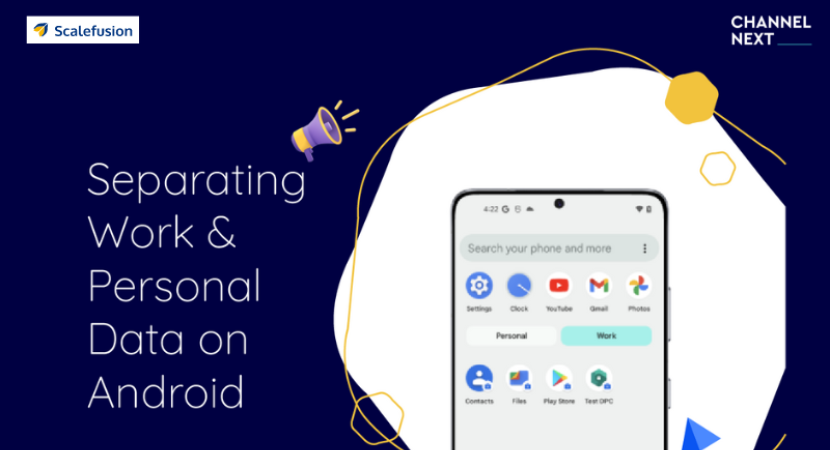
- December 30, 2022 How can you separate your work and personal profile on Android?When smartphones and mobile devices became more popular in the workplace, people used to have two devices. One...By Admin
- December 30, 2022 What is TOPIA?Topia More computers, more software, and dynamic environments lead to more vulnerabilities. The Security and IT teams are put...By Admin
- December 23, 2022 A Complete Guide to Asset Management for Small BusinessAsset management does not necessarily have to involve fixing defective assets. Asset management requires that you have the resources...By Admin
- December 8, 2022 DMARC Policy Overrides: ExplainedDMARC Policy Overrides: ExplainedThis article explains what DMARC policies overrides are and how they work. It also explains...By Admin
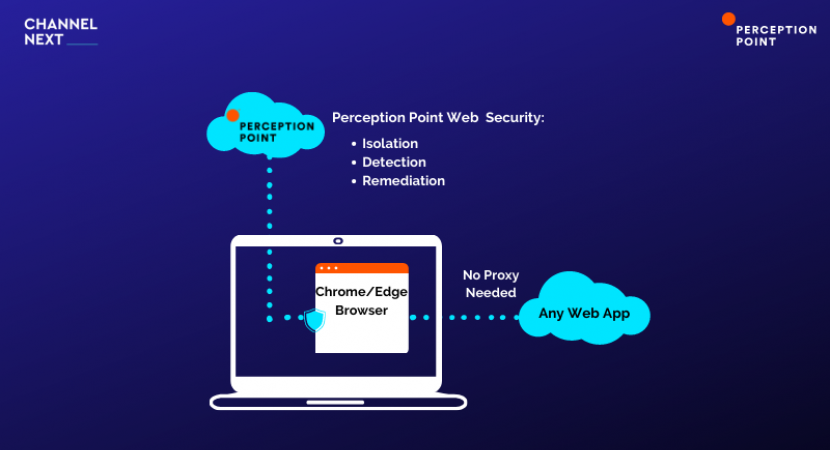
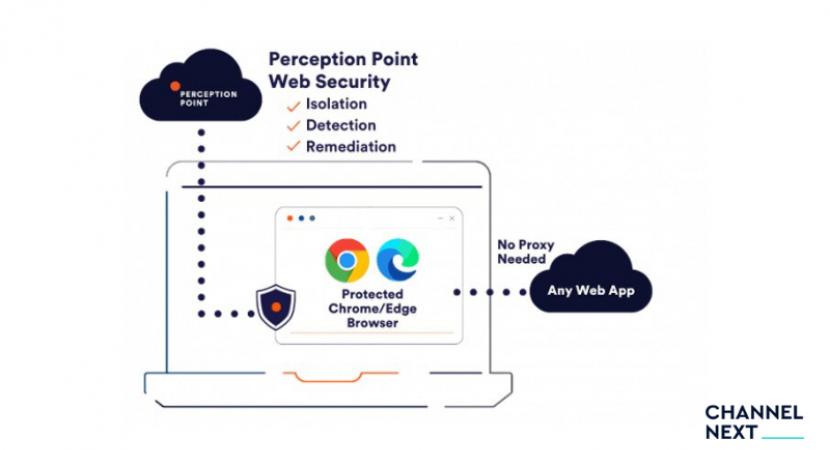
- September 1, 2022 Advanced Browser Security- Perception PointPerception Point is constantly improving its prevention service portfolio for email and collaboration apps such as Office 365,...By Admin
- July 27, 2022 Perception Point Advanced Browser Security detects browser threatsPerception Point has released Perception Point Advance Browser Security, a web security solution that adds enterprise-grade protection to...By Admin
- July 20, 2022 Patch ManagementWhat is Patch Management? A patch management system is a collection of policies or systems that help in identifying...By Admin
- June 6, 2022 What is Mobile Device Security and Why is it importantIn today’s world, Technology is growing rapidly but it also increases the risk of cyber-attacks. From leaking photos...By Admin
- February 3, 2022 SEGs vs ICES SolutionsIn today’s world, fast communication and easy access are something that’s essential in everyone’s life. To ensure this,...By Admin
- January 22, 2022 Endpoint SecurityWith the recurring malware & cyber-attacks happening daily, the quest for a solid and reliable end point security...By Admin
- January 18, 2022 Perception Point Advanced Email SecurityWhat is our primary use case? Perception Point Advanced Email Security scans incoming emails. Our majority of clients are...By Admin
- January 20, 2021 What is DMARC Parser and How can you use itAn online tool called DMARC Parser allows you to translate your DMARC authentication data in a format that...By Admin
- January 20, 2021 Single Sign-On (SSO): Everything You Need To KnowAlthough Single Sign-On (SSO), has been in use by many enterprises for many years, its importance has never...By Admin